Original article posted at IRONSCALES: Phishing websites, also known as spoofed websites, are a very common deception tactic that attackers now rely on to obtain a person’s login credentials to a legitimate website. The operation, commonly known as credential theft is simple: send unsuspecting recipients an email spoofing a trusted brand and persuade them to click on a link that subsequently takes them to a login page where they will be asked to enter their username and password. Once completed, attackers have the information they need to login to a real account and commence with illegal activity, such as credit card fraud, data extraction, wire transfers and more.
While such fraudulent URLs aren’t new, the prevalence and sophistication have increased exponentially. In fact, a recent report by Webroot Security identified nearly a 400% increase in new phishing websites, equating to ~1.5 million coming online per month. This is an incredible number when considering phishing websites only stay active for 4-8 hours on average.
Attackers have turned to phishing websites, most commonly as a means to impersonate the world’s most popular brands, as gateway-level email security and anti-phishing tools have gotten smarter and more efficient at detecting emails with traditional malicious payloads, such as links that deliver automated malware downloads, and malicious attachments. Phishing websites are especially problematic for companies that rely on rules-based email security such as secure email gateways (SEGs), multi AV scanners and sandboxing solutions, as such tools and solutions lack visual anomaly detection capabilities required to assess a fake login page from a legit login page in real-time.
Analyzing 25,000 emails for links to phishing websites
To learn more about the prevalence of phishing websites, IRONSCALES analysts reviewed 25,000 emails in Q3 with verified malicious links and attachments. Since IRONSCALES sits in the mailbox and not at the gateway, the 25,000 emails studied had either bypassed a secure email gateway or cloud email security tool, such as Office 365 Advanced Threat Protection (ATP).
In total, we found that 23% (5,750) of the 25,000 malicious emails included links to active phishing websites. This represents a 5% increase when compared to the previous 90-day period. Of that, the top five most spoofed websites we discovered were:
- Microsoft (37%)
- PayPal (25%)
- HSBC Holdings (8%)
- Adobe (5%)
- Wells Fargo (3%)
- Other (22%)
Why people struggle to identify visual similarities in phishing websites
The success of phishing websites can best be explained by the psychological phenomenon first discovered in the early 1990’s known as inattentional blindness. Defined as an individual failing to perceive an unexpected change in plain sight, inattentional blindness became an internet sensation in 2012 when a video posted asking viewers how many white shirted players passed a ball. Intently focused on the task at hand, more than 50% of the viewers failed to recognize a woman in a gorilla suit in the middle of the picture.
Recognizing the perils of inattentional blindness, adversaries have begun to see the importance of creating attacks that deceive the human brain in addition to defeating technological controls. Yet there are often clear indicators within phishing websites that can help people identify fake URLS should they know what to look for.
Of the 5,750 phishing websites we identified last quarter, each had a visual or verbal anomaly or flaw that wasn’t recognized by technology, such as blurred or resized images or an undue sense of urgency. This is because the closer the page looks to the real one, the easier advanced anti-phishing technology can detect that it’s a fake. Thus, attackers are constantly trying and make phishing websites different enough to defeat technical email controls but similar enough that a human would think it’s legit.
Specifically, we identified five categories to which each phishing website fell into. This included:
- Blurred (45%) – When an image appears blurry and out of focus.
- Resized – (25%) – When an image is appears stretched or elongated.
- Creative – (15%)- When an attacker tries to make a connection through design.
- Retro – (10%) When an image or copy uses outdated branding and messaging .
- Sense of Urgency (5%) – When copy contains uncommon immediacy in copy and calls to action.
Thanks to intentional blindness, most people do not immediately see these visual similarity clues, wrongly assuming the spoofed login page as legitimate and entering their credentials which unbeknown to them are about to be used in a cyberattack.
Preventing phishing website links from laying idle in an inbox
Traditional signature-based email gateway security solutions are challenged to stop these types of attacks as they were designed to scan the source code that lays behind the HTML page in order to match the signatures of previously known attacks. Consequently, savvy criminal groups must strike the right balance between creating spoofed landing pages that look similar enough to legitimate pages to dupe their intended victims but not identical enough to be snared by anti-phishing technologies. By taking a polymorphic approach, attackers can automate and refine the process of deploying pages that do not surpass predefined detection thresholds. By comparing the visual similarity of legitimate landing pages to spoofed ones, computer vision enabled solutions provide a critical additional layer of defense since they do not rely on simple pattern matching technologies.
About IRONSCALES
IRONSCALES is the future of phishing protection, incubated inside the world’s top venture program for cybersecurity and founded by alumni of the Israel Defense Forces’ elite Intelligence Technology unit. We offer security professionals and end users an AI-driven, self-learning email security platform that provides a comprehensive solution to stop tomorrow’s phishing attacks today. Using the world’s most decentralized threat protection network, our platform accelerates the prevention, detection and remediation of phishing attacks already inside your email with threat removal times in seconds, not minutes or hours. We give organizations of all sizes complete anti-phishing protection against any type of phishing attack, right now. Visit www.ironscales.com to learn more about The Power of Now.
To learn more about how we use computer vision to protect against fake login pages, read IRONSCALES blog Fight Phishing & Credential Theft with AI
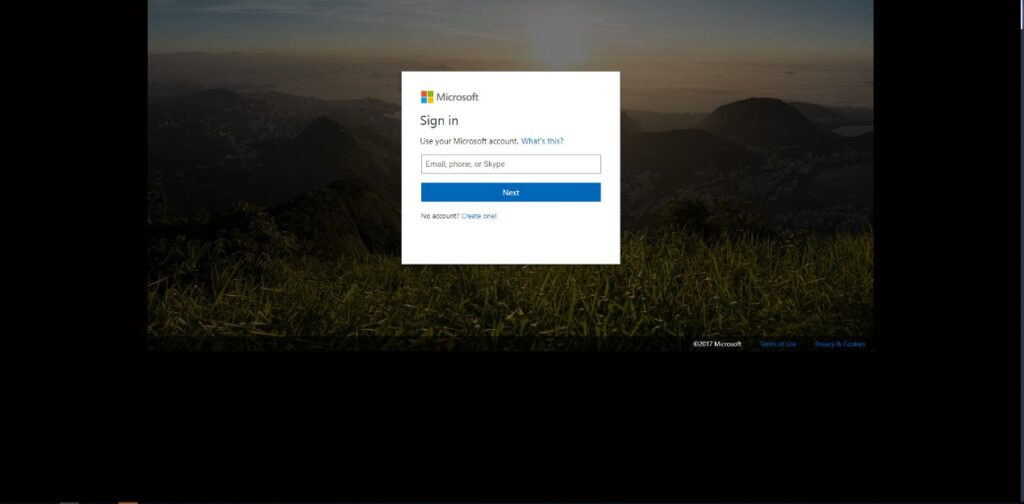
Some examples of fake Office 365 login pages captured by IRONSCALES’ visual similarity detection.
Resize:
Users are expecting the login box and they are focused on it, not noticing the background – this is exactly what the attacker is relying on since they can change it slightly to evade visual similarity detection.