Last week the U.S. Federal Trade Commission reported that approximately $12 million was lost to coronavirus-related scams according to consumer reports reviewed this year. With over 20,000 Cyberattacks per day in April 2020, its is obviously that attackers are taking advantage of the pandemic to lure consumers using various attack vectors including social media, phone calls, text messages and phishing emails.
Security telemetry data obtained depicts that since March there had been a surge in the number of coronavirus outbreak related phishing emails and at the beginning of February 2020, a sudden spike recorded in the registration of domains associated with fraudulent COVID-19 themed extortions and financial scams surrounding the purchase of medical supplies including face masks and PPEs as an example.
How does Cybercriminals work?
Cybercriminals send emails claiming to be from legitimate organizations with information about the coronavirus. The email messages might ask you to open an attachment to see the latest statistics. If you click on the attachment or embedded link, you’re likely to download malicious software onto your device. The malicious software — malware, for short — could allow cybercriminals to take control of your computer, log your keystrokes, or access your personal information and financial data, which could lead to identity theft. The coronavirus — or COVID-19, the name of the respiratory disease it causes — has affected the lives of millions of people around the world.
It’s impossible to predict its long-term impact. But it is possible to use Anti Phising tools that helps your organization protect yourself against coronavirus-related scams.
How do I spot a coronavirus phishing email? Examples
Coronavirus-themed phishing emails can take different forms, including these.
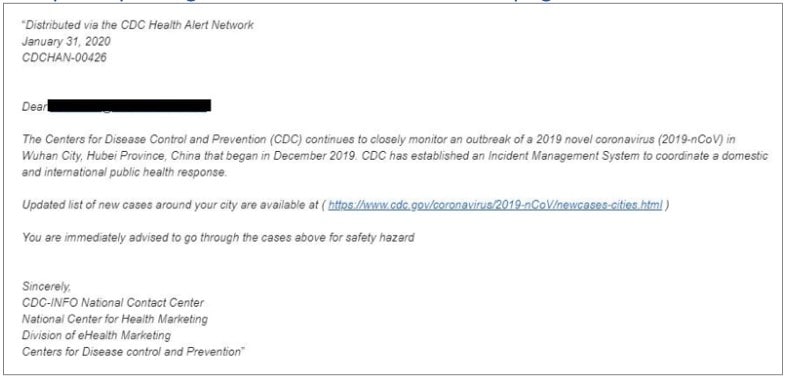
CDC alerts. Cybercriminals have sent phishing emails designed to look like they’re from the U.S. Centers for Disease Control. The email might falsely claim to link to a list of coronavirus cases in your area. “You are immediately advised to go through the cases above for safety hazard,” the text of one phishing email reads.
What do the emails look like? Here’s an example of a fake CDC email. (All examples below come from the U.S. Health and Human Services website.)
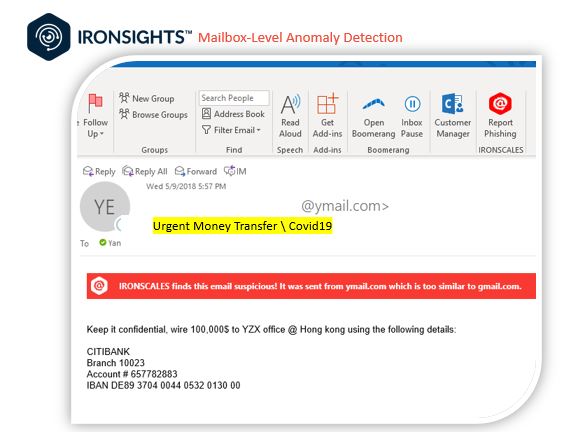
Money request emails. Phishers have sent emails that offer purported medical advice to help protect you against the coronavirus. The emails might claim to be from medical experts near Wuhan, China, where the coronavirus outbreak began. “This little measure can save you,” one phishing email says. “Use the link below to download Safety Measures.”
Here’s what a fake money request email will look like.
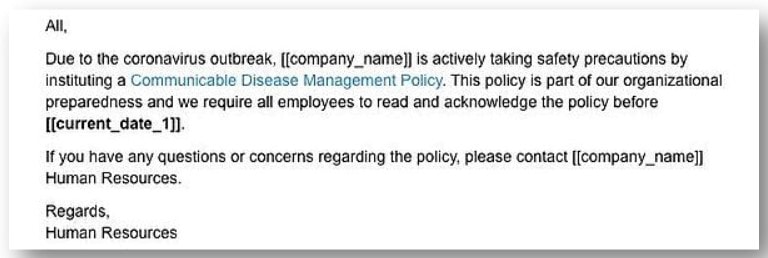
Workplace policy emails. Cybercriminals have targeted employees’ workplace email accounts. One phishing email begins, “All, Due to the coronavirus outbreak, [company name] is actively taking safety precautions by instituting a Communicable Disease Management Policy.” If you click on the fake company policy, you’ll download malicious software.
Here’s an example.
How do I avoid scammers and fake ads?
Scammers have posted ads that claim to offer treatment or cures for the coronavirus. The ads often try to create a sense of urgency — for instance, “Buy now, limited supply.”
At least two bad things could happen if you respond to the ads.
One, you might click on an ad and download malware onto your device or endpoint.
Two, you might buy the product and receive something useless, or nothing at all. Meanwhile, you may have shared personal information such as your name, address, and credit card number.
Bottom line? It’s smart to avoid any ads seeking to capitalize on the coronavirus.
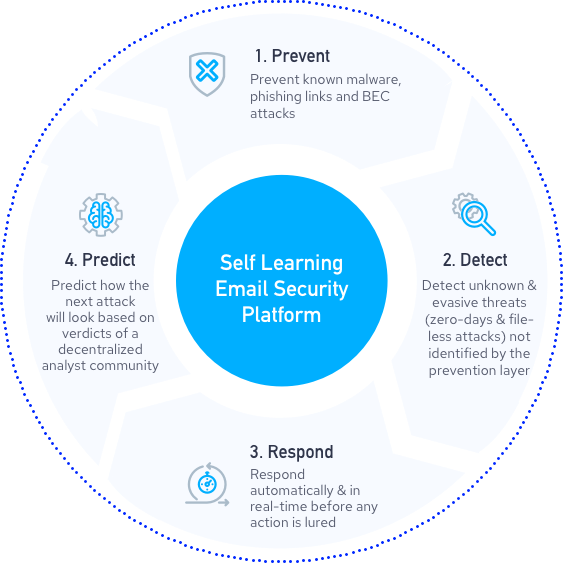
How IRONSCALES helps you recognizing and avoiding phishing emails

Here are some ways IRONSCALES platform can help you recognize and remove Covid19-themed phishing emails.
Like other types of phishing emails, the email messages usually try to lure you into clicking on a link or providing personal information that can be used to commit fraud or identity theft. Here’s some ways IRONSCALES will prevnrt your organization from getting tricked.
- Alerting of unusual online requests for personal information. A coronavirus-themed email that seeks personal information like your Social Security number or login information is a phishing scam. Legitimate government agencies won’t ask for that information. Never respond to the email with your personal data.
- Automation URL and email address scan. IRONSCALES will inspect your links by scanning the URL ongoingly to see where it leads and if the link has changed. Sometimes, it’s obvious the web address is not legitimate. But keep in mind phishers can create links that closely resemble legitimate addresses.
- Identify spelling and grammatical mistakes. If an email includes spelling, punctuation, and grammar errors, it’s likely a sign you’ve received a phishing email. IRONSCALES will create an alert inside your inbox.
- FEDERATION Look for generic greetings. Phishing emails are unlikely to use your name. Greetings like “Dear sir or madam” signal an email is not legitimate. IRONSCALES will automatically identify and block these false mails.
- Admin will remove emails that insist you act now. Phishing emails often try to create a sense of urgency or demand immediate action. The goal is to get you to click on a link and provide personal information — right now.
Where can I find legitimate information about the coronavirus?
It’s smart to go directly to reliable sources for information about the coronavirus. That includes government offices and health care agencies.
Here are a few of the best places to find answers to your questions about the coronavirus.
Centers for Disease Control and Prevention. The CDC website includes the most current information about the coronavirus. Here’s a partial list of topics covered.
- How the coronavirus spreads
- Symptoms
- Prevention and treatment
- Cases in the U.S.
- Global locations with COVID-19
- Information for communities, schools, and businesses
- Travel restrictions
World Health Organization. WHO provides a range of information, including how to protect yourself, travel advice, and answers to common questions.
The World Health Organization will:
- Never ask for your username or password to access safety information
- Never email attachments you didn’t ask for
- Never ask you to visit a link outside of www.who.int
- Never charge money to apply for a job, register for a conference, or reserve a hotel
- Never conduct lotteries or offer prizes, grants, certificates or funding through email.
National Institutes of Health. NIH provides updated information and guidance about the coronavirus. It includes information from other government organizations.

Cyber threats are evolving, and so are we. Stop Tomorrow’s Phishing Attacks, Today.
The best time to stop phishing emails is before they hit the mailbox, yet 25% of attacks get past existing defenses. With 82 seconds on average until the first click is lured, the second best time is now.
Herman Technologies is a proud partner of IRONSCALES, a comprehensive pre-post-delivery Anti Phishing platform, designed to quickly detect bad emails slipping through the prevention layer and responding to them automatically in seconds, blocking them for good.
Leveraging on both AI and real-time human intelligence with the speed and simplicity to stay ahead of new threat
Info@herman-technologies.com \IRONSCALES