
Transforming Secure Access for the Remote Workforce
Say goodbye to the legacy hardware of the past and discover the benefits of our leading Secure Access Service Edge (SASE).
Herman Technologies is a proud partner of Perimeter 81, The SASE Secure Access Service Edge platform that combines network and security functionality into a unified global cloud-based service.
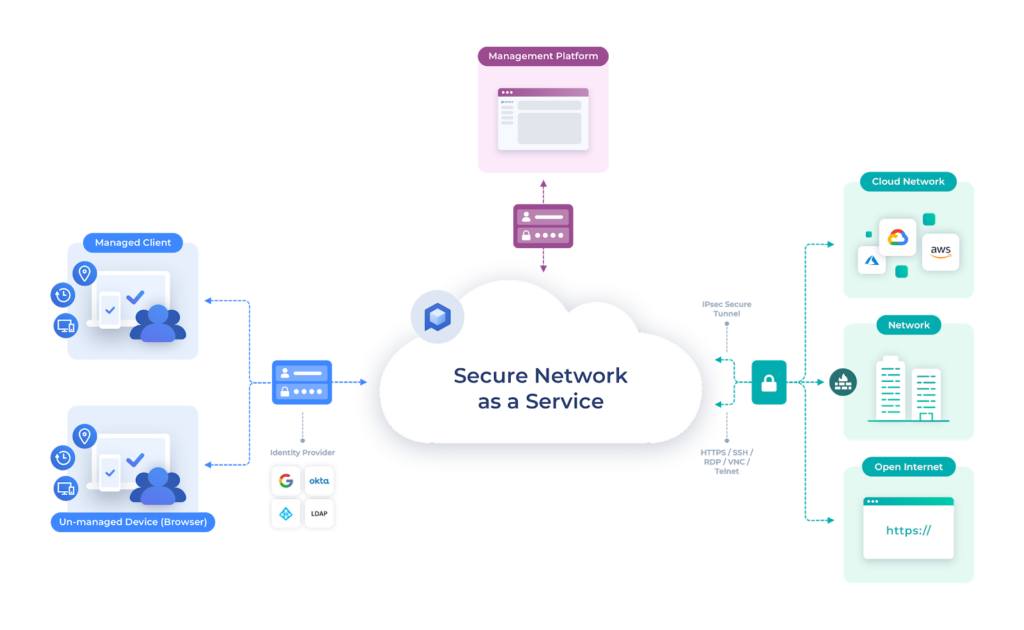
One Complete Network Security Platform
No more manual configuration. No more hours of setup. Fully build, manage and secure your network from our multi-tenant cloud.

Certified Soc 2, GDPR, HIPAA and ISO 27001 Compliant
We adhere to the highest standards of software security compliance, so you can rest assured that your organization’s data remains fully protected.
Learn More

What is Secure Access Service Edge (SASE)?
The cybersecurity and network security solution space is highly segmented, with endless options and solutions offered by security vendors. Instead of simplifying the consumption of cybersecurity, these services are complicating what should be a smooth transition for integrating solutions in an organization’s network environment. The entire cybersecurity space needs to come together to provide a more holistic cybersecurity approach, and this is where SASE comes in.
Secure Access Service Edge (SASE) is the cloud architecture model that combines the different functions of network and security solutions into a unified cloud security platform to be delivered as a service without any or minimal hardware and appliances involved. This new model allows IT teams to easily connect and secure all of their organization’s networks and users in an agile, cost-effective and scalable way.
What does a SASE Model Do?
A Secure Access Service Edge (SASE) platform provides organizations the opportunity to simply connect to a single secure network where they can gain access to physical and cloud resources – no matter their location. SASE enables IT security solutions to provide a more holistic and agile service for business networking and security for its customers. What makes SASE innovative and disruptive is the idea of how it will transform the way network security is consumed over traditional products and cloud services.
Use Cases
Perimeter 81’s SASE platform combines network and security functionalities into one unified network security service solutionUnified Cloud Management
Our SASE platform unifies a range of network and endpoint security solutions managed & delivered through the cloud. This single cloud management platform provides consolidated, user centric networks & granular policy management for organizations of all sizes.
Zero Trust NaaS
A multi-region cloud network provides a comprehensive set of converged secure network capabilities, delivered and managed over our multi-tenant cloud, providing a secure and highly-scalable network for organizations everywhere.
Firewall as a Service
A SASE platform offers a Firewall as a Service which protects organization’s site-centric networks from potential threats, while implementing modern security features for next-gen firewall.
Cloud Sandboxing
A SASE platform includes Cloud Sandboxing where we analyze unknown files for zero-days and advanced threats.
A platform delivers full sandbox protection on and off your network.
A SASE platform delivers DNS Security that automatically prevents millions of malicious domains which is identified with real-time analysis with global threat intelligence. It predicts and stops malicious domains with algorithm-based malware with instant enforcement.
SaaS Security
A SASE platform ensures that your organization has SaaS security including Office 365, Google Drive, Dropbox and others.
Endpoint Security
A SASE platform includes complete endpoint security for your organization. We deliver multiple endpoint protection capabilities, including next-generation malware protection and support for visibility into encrypted traffic.
Endpoint Compliance
With Endpoint Compliance, our client scans for security features like Firewall, Anti-Virus, Windows patches, Processes and more. This results in a more secure network and eliminates security threats in one’s network.

The Four Main Characteristics of the SASE Model
Gartner defined that a SASE service consists of four main characteristics.
Identity-driven
With a least-privileged strategy and strictly enforced access control, organizations will be able to control interactions with resources based on relevant attributes, including application access, user and group identity and the sensitivity of the data being accessed.Cloud-based architecture
The SASE model architecture includes implementing different key cloud capabilities which will provide an agile, holistic, adaptive, self-updating platform. This will provide organizations an efficient and easily adaptable platform for their business needs no matter where they are located.Supports all edges
SASE creates one network for the entire organization’s resources — data centers, branch offices, cloud resources, and mobile and remote users. For example, SD-WAN appliances support physical edges while mobile clients and clientless browser access connect users on the go.
Globally distributed
To ensure complete networking and security abilities globally and on the go, SASE platforms must be globally distributed to organizations. This includes delivering a low-latency service to enterprise edges.
Discover How The SASE Model Can Transform Your Organization
With Perimeter 81, we are providing secure, private and unrestricted Internet access to businesses. To do so, we are transforming traditional network security technology with one unified Zero Trust Secure Network as a Service.
Our Secure Access Service Edge (SASE) platform offers:
- Complete visibility
- Precise segmentation
- A user-centric experience
- Increased security
- A highly scalable solution
- Simple transition to cloud environments

What is the Difference Between VPN and Zero Trust Network Architecture?
VPNs, or Virtual Private Networks, are vastly different from networks built with Zero Trust architecture. VPNs are a site-centric solution which enables organizations to create secure, encrypted tunnels between remote employees and crucial network resources. Access via a VPN signifies that the user is automatically trusted with these resources, while Zero Trust networking is a security model that removes the idea of trust. This means privileged network access and policy-based segmentation but also constant monitoring of all individuals on the network, regardless of their status or role.
